Project 2
I was really happy with my first project and decided to focus on aspects of the Internet again for my second project. This time, I wanted to look at the potential implications of malware.
Email is an amazing new, disruptive communication medium. People can more easily and cheaply communicate with people on the other side of the world than ever before. It's also awesome that people can do so any time of the day, but it's unobtrusive. In this way, it differs from, for example, a phone; If you're at all concerned about politeness, calls can only be made during certain hours of the day.
Another aspect of email is the speed at which an individual can communicate with large groups of people. This was the origin of spamming and phishing. On the software side of things, there are Trojans, worms, viruses, and other shady schemes collectively called malware. (Many of these terms are used interchangeably in a way that's not accurate.)
The New Problem
When trying to come up with a project topic, I heard about a new method for spreading malware. It is best summed up in this blog post from F-Secure, a Finnish security company:
A year or two ago, the malware author's preferred way of spreading their wares was via e-mail attachments. We all remember mass outbreaks like Bagle, Mydoom and Warezov.
Well, sending EXE attachments in e-mail doesn't work anymore. Almost every organization is now dropping such risky attachments from their e-mail traffic.
So virus writers have made a clear shift away from e-mail attachments to the Web: drive-by-downloads. This attack often still starts with an e-mail spam run; there's just no attachments in the e-mail anymore as it has been replaced by a web link.
Some of these malicious web sites use exploits to infect you just by visiting a web page, others use compelling stories to fool you into downloading and running a program from the page.
Many have missed this shift of attacks from e-mail to the web. There's a lot of companies measuring their risk of getting infected by looking at the amount of stopped attachments at their e-mail gateway. Those numbers are definitely going down, but the actual risk of getting infected probably isn't.
Those organizations that are not scanning their web traffic for malware should seriously consider starting to do it, right now.
However, virus writers are moving again. We're now seeing more and more malicious e-mails that link to malware — not via HTTP but via FTP links.
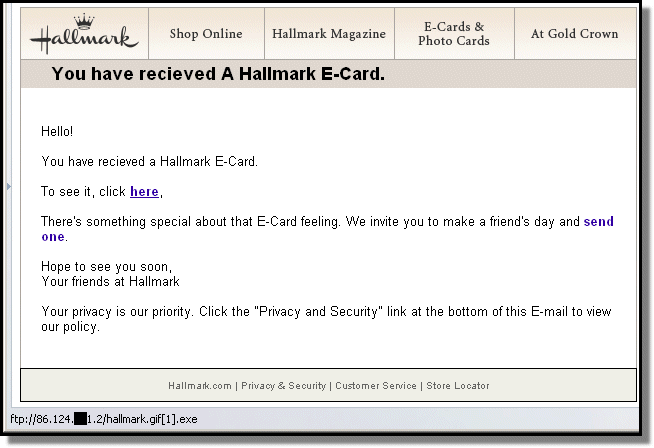
Case in point, a fake Hallmark greeting card spam we saw today:
As you can see, the link takes you to an owned computer which has an FTP site setup on it.
And when the executable is downloaded, it turns out to be a Zapchast mIRC-bot variant.
Setting Up
I sent out a mass email to about 100 addresses. Accounting for duplicates and bounced emails, around 70 different people actually received the email—some family, some close friends, some bosses and professors and colleagues. Some people are people I've kept in touch with and others not so much. I used a newsletter software to do it, but it just looked like a normal email (except that it was in html, but most email softwares can handle that).
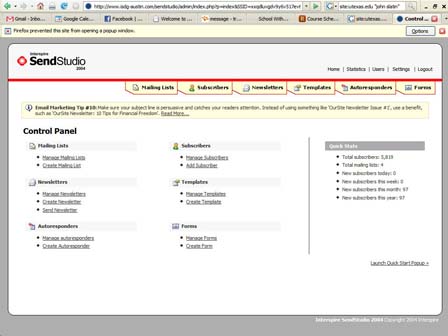
The Email
In the email, I talked briefly about some recent successes that my start up company, Vesper Web Design, has had—a couple contests that we won. I kept the email super generic so that it didn't feel too personal and could apply to all the different people that I sent it to. In this way the email was a little awkward and nonspecific, perhaps just a little off, much like spammy emails do.
This is what the email said:
Hi. I just wanted to drop you a line and let you know about the recent success of my start up company, Vesper Web Design.
First, I want to just say thank you for all your support. We couldn't have done it without the kindness and teachings of those we've encountered along the way.
In the past few weeks, we've learned that we won two competitions against other firms from across the state.
We won first place in the State Shootout sponsored by Knowbility, a non-profit group which promotes accessibility on the Web. They encourage people to code Web sites that can be used by all kinds of users, including those with various types of disabilities who surf the Web very differently.
Last night, we learned that we also placed third in the Interactive Accessible Internet Rally, a contest sponsored by the same group.
Please check out the [start link] Deda Divine Fabulous Jewelry site [end link], which won AIR Interactive, and the [start link] BDPA-Austin site [end link], which won the state competition. We're constantly trying to refine our working process and are very open to feedback.
For more information about Vesper Web Design, check out [start link] our company's site [end link].
Tracking the Responses
I included three links—to the two web sites that won the contests and to the homepage of my company. I used http://www.tiny.cc/ to mask the URL that they were really going to, but clearly indicated their destination. The links generated by www.tiny.cc are used by people in all kinds of industries to track hits and create shorter URLs for sharing. For example, one www.tiny.cc URL that I generated was http://tiny.cc/airinteractive331 but actually redirected to www.dedadivinefabulousjewelry.com.
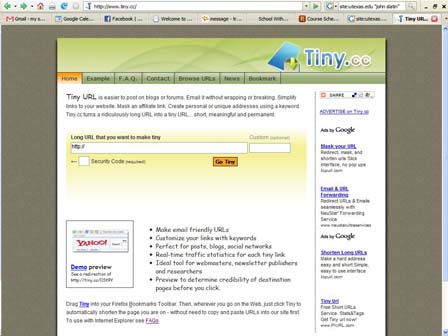
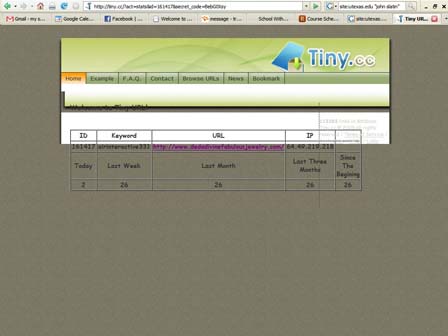
Using the data from www.tiny.cc and the newsletter software, I have information on when people opened the emails and when or if they clicked the links. I also have records of whether people replied to me and, if so, when. I intend to come up with some way of representing this graphically. Whether or not people replied to me is another level of distinction.
I should make an aside note about my methods before I continue. Everyone who visited any of the links were tracked by the www.tiny.cc generated URL. However, some email clients inhibited the newsletter tracking methods from doing their job. For example, the number of people who opened the email were tracked by an embedded PHP script inside an image (img) tag.
To understand how the tracking links worked, see the email's html code below:
<div>
<p>Hi. I just wanted to drop you a line and let you know about the recent success of my start up company, Vesper Web Design.</p>
<p>First, I want to just say thank you for all your support. We couldn't have done it without the kindness and teachings of those we've encountered along the way.</p>
<p>In the past few weeks, we've learned that we won two competitions against other firms from across the state.</p>
<p>We won first place in the State Shootout sponsored by Knowbility, a non-profit group which promotes accessibility on the Web. They encourage people to code Web sites that can be used by all kinds of users, including those with various types of disabilities who surf the Web very differently.</p>
<p>Last night, we learned that we also placed third in the Interactive Accessible Internet Rally, a contest sponsored by the same group.</p>
<p>Please check out the <a href="http://www.isdg-austin.com/sendstudio/users/link.php?UserID=5915&Newsletter=13&List=4&LinkType=
Send&LinkID=33" target="_blank">Deda Divine Fabulous Jewelry site</a>, which won AIR Interactive, and the <a href="http://www.isdg-austin.com/sendstudio/users/link.php?UserID=5915&Newsletter=13&List=4&LinkType=
Send&LinkID=34" target="_blank">BDPA-Austin site</a>, which won the state competition. We're constantly trying to refine our working process and are very open to feedback.</p>
<p>For more information about Vesper Web Design, check out <a href="http://www.isdg-austin.com/sendstudio/users/link.php?UserID=5915&Newsletter=13&List=4&LinkType=
Send&LinkID=32" target="_blank">our company's site.</a>.</p>
<img src="http://www.isdg-austin.com/sendstudio/users/sendopen.php?MemberID=5915&SendID=8&Type=Send">
</div>
Because many email programs and webmail services, like gmail, suppress the images until users opt to see them, not every email opening was successfully tracked. The point is that this was not an exact process and I admit that there is some intrinsic error.
What I Found
I set up two different groups. One for the people emailed who I know well and another for those that I don't. The people in this group are mostly people that I haven't talked to in years and/or don't know the name of my company, so if they clicked on the links they did so with less of a reasonable expectation that they weren't falling victim to spam.
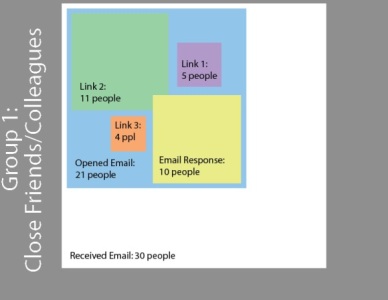
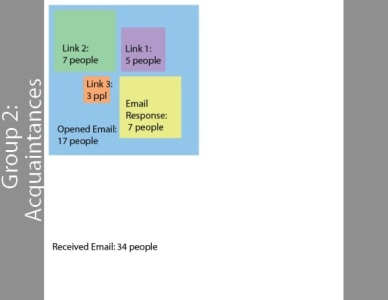
The www.tiny.cc URLS could have redirected to an FTP URL instead of a HTTP URL, which then could have downloaded malware (virus, trojans, or whatever) on to any of the link clickers' computers.
Malware can easily/quickly viruses can spread and destroy. There is a certain level of trust, I think, which may be misplaced, when you get an email from someone you know or used to know. They're machines could be compromised by malware, which can send email to everyone in an account's contact list.
UT's Response
After completing my project, I saw an email that UT sent out about the fake Hallmark card email. While it's good that the University is keeping its poeple informed, I found it very disappointed that the email didn't address the real issue-- the dangerousness of FTP links.